Tips for Reclaiming Your Digital Privacy in 2025
Maintaining online privacy in today’s world is nearly impossible without completely disconnecting—and even then, friends and family may inadvertently expose your information through their own weak security practices. Because of this, many people see the effort as futile and don’t even bother. But I completely disagree. A core principle in cybersecurity is that the absence of perfect security should never prevent you from making meaningful improvements. Reducing the number of entities that can track you or access detailed personal information is always a worthwhile effort. And most importantly: you must establish privacy and secure habits before you actually need them.
With the current administration accelerating its slide toward authoritarianism, I thought it’d be wise to share a few simple steps that can make tracking you significantly harder. My goal is to offer practical tips that the average person can realistically adopt—small changes that provide meaningful benefits without disrupting daily life.
Why You Should Care
The Wall Street Journal recently released an article entitled Federal Agencies Use Cellphone Location Data for Immigration Enforcement which includes a passage:
U.S. Immigration and Customs Enforcement, a division of DHS, has used the data to help identify immigrants who were later arrested, these people said. U.S. Customs and Border Protection, another agency under DHS, uses the information to look for cellphone activity in unusual places, such as remote stretches of desert that straddle the Mexican border, the people said.
There is no way to buy just criminal data, and the thought of DHS tracking American citizen's location without a warrant is gross and ripe for abuse.
Added Benefit: Making Cyber Criminals live's Harder
While doing recon on a target, adversaries will often times use some of these exact services to collect data on employees of their target organization. There was a great Episode (thought I don't recall which) of the Darknet Diaries Podcast where the red team did exactly this and found an employee of a victim organization was really into supporting a specific charity, and used this against the organization in a target vishing/phishing attack and were met with great success.
More elegantly put via Mitre ATT&CK ID T1589:
Adversaries may gather information about the victim's identity that can be used during targeting. Information about identities may include a variety of details, including personal data (ex: employee names, email addresses, etc.) as well as sensitive details such as credentials.
Adversaries may gather this information in various ways, such as direct elicitation via Phishing for Information. Information about victims may also be exposed to adversaries via online or other accessible data sets (ex: Social Media or Search Victim-Owned Websites).[1][2][3][4][5][6][7][8] Gathering this information may reveal opportunities for other forms of reconnaissance (ex: Search Open Websites/Domains or Phishing for Information), establishing operational resources (ex: Compromise Accounts), and/or initial access (ex: Phishing or Valid Accounts).
By opting out you can make it much harder and really make them work a little extra to gather information on you.
Note: This of course will not stop cyber criminals, stalkers, or the Government from tracking you. This will only minimize what's publicly out there to make it that much more difficult. If you have reason to believe you are actively being targeted, or may be in the future - consider contacting law enforcement or working with a professional organization such as the EFF.
Databrokers and Opting Out
Data brokers are companies that collect and sell personal information—often without your direct consent. They obtain this data through various means, including purchasing it from businesses, scraping public records, and embedding trackers in apps and websites. These brokers are the reason why searching your name online often leads to unsettling results on background check sites, revealing details like your phone number, address, and relatives.
Unfortunately, this practice is legal, and opting out is a manual, time-consuming process. Even worse, many of these companies “accidentally” reacquire your data over time, meaning you may need to opt out repeatedly to maintain your privacy.
Paid Services
Because of the persistent nature of data collection, I personally use multiple opt-out services rather than relying on just one—though I realize that’s not an option for everyone. If you’re considering a paid service, Consumer Reports conducted a study to evaluate the effectiveness of different removal services, providing objective data rather than anecdotal recommendations.
So I recommend if you're going to choose a service, to take a data driven approach and pick based on the results of the Consumer Reports study. This report didn't exist whenever I first signed up for my services so here's the experience I've had with a couple of paid services that seem to have worked well:
DeleteMe
DeleteMe uses a manual, human-reviewed process to remove your personal information from various databases. They provide regular reports detailing their takedown progress, and in my case, I noticed a significant reduction in the visibility of my personal data when searching my name online. However, because new data broker sites appear frequently, a fully manual approach may not be sustainable long-term.
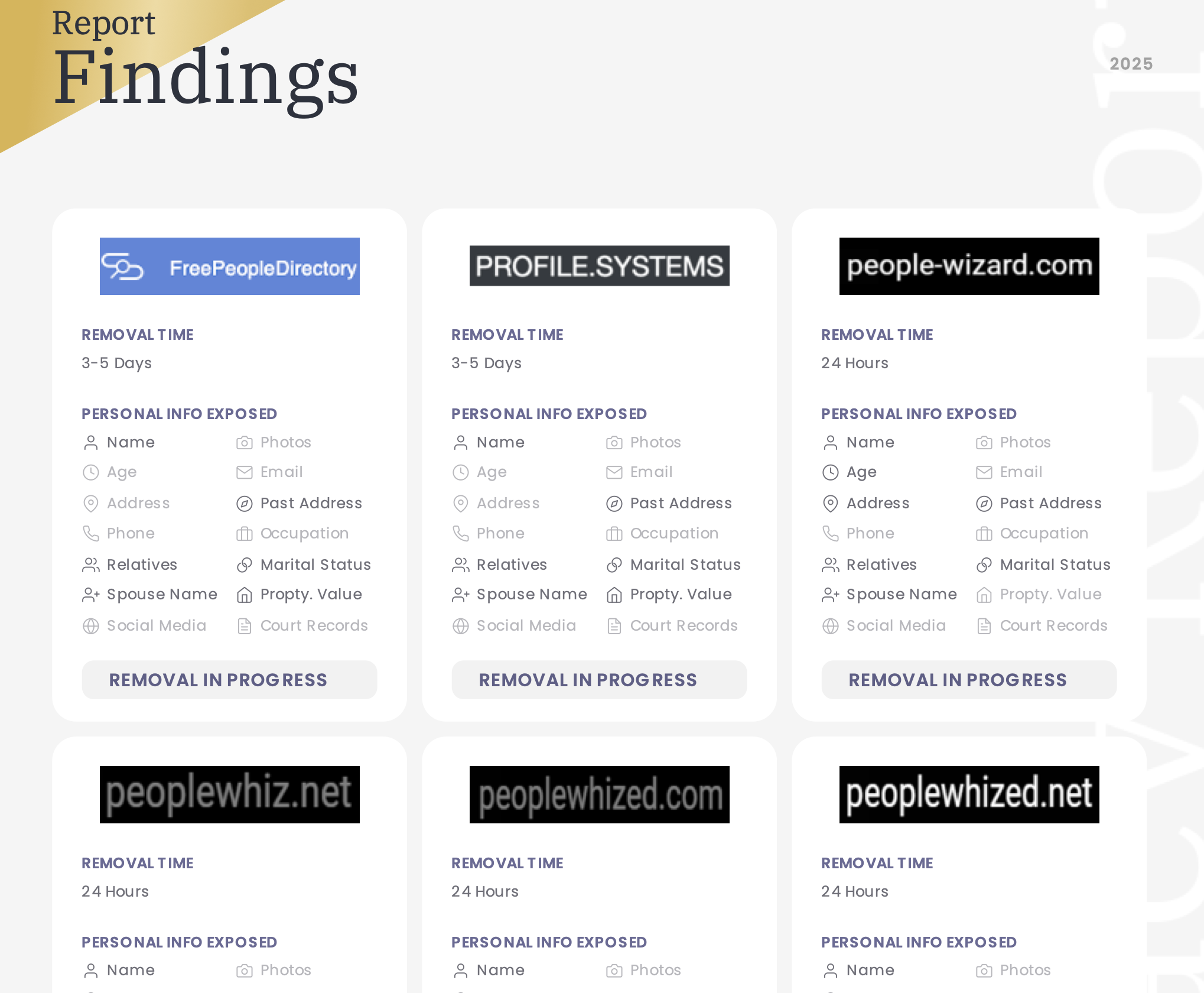
You can sign up on the DeleteMe site, or if you want to support me, here's my referral code.
Incogni
Incogni offers a more automated approach, which complements DeleteMe’s manual efforts. By combining both services, I aim for broader coverage and more consistent removals.
If you’re serious about minimizing your digital footprint, using a service—or a combination of them—can save you time and effort compared to the tedious manual opt-out process.
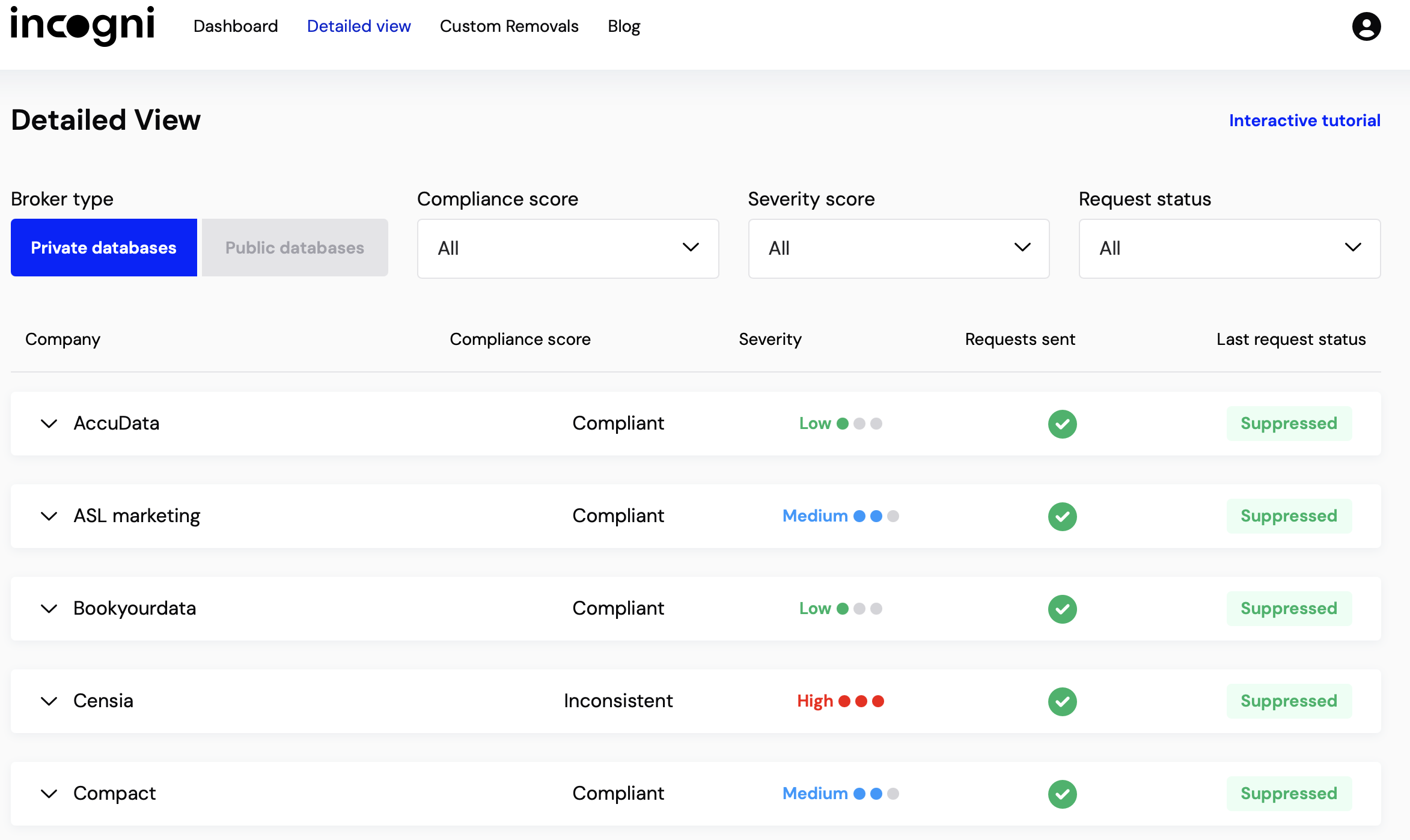
You can sign up for Incogni, or again if you'd like to support me here's my referral code.
Free Services and DIY
Manually opting yourself out of data broker sites will ultimately give you the best results in the long run, but it's an incredibly time-consuming process. Worse yet, your information can often reappear on these sites “unintentionally,” requiring ongoing maintenance.
Thankfully, someone has compiled a comprehensive opt-out resource: the Big Ass Data Broker Opt-Out List. This guide provides direct links and instructions for removing your data from numerous brokers.
Additionally, Consumer Reports has developed an app called Permission Slip. It offers both a paid service—reportedly quite effective—and a free, semi-manual option that simplifies opting out of multiple services. One of its standout features is guiding users through the process of downloading their personal data from social media platforms and opting out of data sales, making it accessible even for those unfamiliar with privacy management.
Phone Applications/Built-in OS Privacy Opt-Outs
Both iOS and Android come with built-in tracking features that collect data for analytics, advertising, and personalization. Disabling these settings can help improve privacy, but the options are often buried deep in system settings. Below are official guides and third-party resources to help you opt out effectively.
iOS Privacy Opt-Out Guide
- Turn off App Tracking Transparency: Apple Guide
- Disable Personalized Ads & Location Tracking: Apple Privacy Settings
- Limit Data Sharing with Apple & Apps: Apple Privacy Portal
Android Privacy Opt-Out Guide
- Disable Google Ad Personalization: Google Ads Settings
- Turn Off Location Tracking & History: Google My Activity
- Restrict App Permissions & Background Data Collection: Android Privacy Settings
Automation & Bluetooth/WiFi Privacy
A recent study from the University of California, San Diego revealed that Bluetooth signals can be used to track smartphones. To mitigate this, consider automating your device settings using tools like Apple's Shortcuts. You can configure your phone to automatically disable Bluetooth and WiFi when leaving home or trusted locations and re-enable them when returning—eliminating the need to manage it manually.
Of course, you can always turn these settings back on manually if needed.
Use Encryption
Enable Apple's Advanced Data Protection to ensure all data stored in iCloud is fully encrypted—if cloud storage is necessary at all.
To reduce the risk of fraud and man-in-the-middle (MITM) attacks, enable Apple's Contact Key Verification.
For secure communications, use end-to-end encrypted messaging and email services like Signal and ProtonMail. Keep in mind that email encryption only applies to messages between ProtonMail users. When sending sensitive emails to non-ProtonMail users, use Password-Protected Emails to set expiration dates and prevent long-term storage.
Use Safari's Private Relay
iCloud Private Relay is a privacy feature in Safari designed to prevent tracking of your browsing activity. It works by routing your internet traffic through two separate relays:
- The first relay, operated by Apple, hides your IP address from the website you're visiting.
- The second relay, run by a third-party provider, assigns a temporary IP address and connects you to the site.
This ensures that no single entity—including Apple—can see both your identity and the sites you visit.
Use Private, Temporary Email Addresses
Apple, ProtonMail, and Fastmail all offer services for creating unique, disposable email addresses. These prevent websites from tracking your real email and help mitigate spam and data breaches.
With Apple's "Hide My Email," you don’t need an @icloud.com address—it can forward to any email account you choose. Using unique addresses for each service can help protect against accidental exposure, as seen in incidents like the Ashley Madison breach, where leaked emails linked users to personal or sensitive accounts.
Use a Password Manager
A strong password manager, such as 1Password or the built-in managers on iOS and Android, enhances both security and privacy. Using the same password across multiple accounts risks exposing your identity if your credentials are leaked in a breach. Unique passwords prevent attackers from linking your accounts together based on reused credentials.
Prevent Weather Apps from Tracking Your Location
Many third-party weather apps have been caught selling location data. To reduce this risk:
- Use the built-in weather apps on iOS or Android instead of third-party alternatives if possible.
- Instead of granting live location access, manually enter zip codes for areas you frequent.
This prevents weather services from continuously tracking your real-time location while still allowing you to check the forecast for relevant locations.
Other Opt-Outs to Consider That Aren’t Traditionally Covered
Some forms of data collection fall outside what paid opt-out services typically handle, including car data, credit card transactions, and financial accounts. These require more manual intervention but are just as important to protect your privacy.
Cars
Modern vehicles collect extensive data on drivers, from location history to driving habits. While it may sound absurd, opting out of your car’s data collection is necessary. If you’re in the market for a new car, data privacy should be a consideration before purchase. Mozilla maintains an excellent guide on what data different manufacturers collect and how to opt out where possible.
Credit Cards & Bank Accounts
Financial institutions collect and share significant amounts of personal data. While privacy policies differ, here are direct links to opt-out options for some major issuers:
-
- To opt out, email Apple’s privacy team at dpo@apple.com with the subject line “Apple Relationship Data and Apple Card.”
-
- Use the Data Analytics Opt-Out page.
-
- To opt out of affiliate marketing and creditworthiness sharing, call 1-800-225-5202.
-
- Visit American Express Communications Preferences or call 1-855-297-7748.
It's the Small Things
Something that's really obvious but some people don't think about or consider is that most companies don't actually need your real name, address, name, age, or gender or anything else. Consider if the company in question actually needs the data they are requesting, and if not there is no hard in feeding them false and competing information to companies when signing up where things like e-commerce are unlikely to happen or other sort of services where accurate information may actually be a requirement.
Closing
The fact that you have to take these steps yourself is ridiculous. The burden of protecting personal data shouldn’t fall on individuals—there should be strong privacy laws that prevent this level of data exploitation in the first place. If you agree, consider reaching out to your representatives and advocating for better data privacy protections in the U.S.
That said, don’t let the sheer volume of tracking deter you from making meaningful improvements. You don’t have to be perfectly private to be significantly more private. Even small steps—opting out where possible, using encrypted communication, and limiting unnecessary data exposure—can make a real difference in protecting your personal information.

