The Power of Proactive Cybersecurity with Domain and TLS Monitoring
It is often mistakenly believed that defenders cannot gain visibility into the early stages of the Cyber Kill Chain before the delivery phase. However, monitoring during the weaponization phase is one of the most effective and cost-efficient proactive prevention strategies an organization can implement—a rare combination in this field. By scrutinizing TLS Certificate Transparency logs and new domain registrations, organizations can detect and preempt malicious activities. This proactive approach enables immediate alerts when a domain mimicking your own is identified, allowing for swift actions such as takedown requests to service providers and blocks in internal security tools within the network. These actions can prevent the domain from ever being effectively used against your organization or clients, while also raising the bar it takes to attack your organization. In this article, we will explore how these monitoring techniques can serve as powerful tools for detecting and preventing threats, including those posed by advanced persistent threats (APTs) like Scattered Spider. We will review real-world attacks to illustrate how these controls can provide early warnings and strengthen your cybersecurity defenses.
Transparency: The recent CrowdStrike outage saw a surge in domains registered looking to impersonate CrowdStrike to take advantage of the situation which is what inspired this post. During my tenure at Soteria, I worked on a product that focused on brand reputation monitoring. Given my firsthand experience with its effectiveness, I reached out to them, and they have graciously agreed to sponsor this post. I highly recommend checking out their brand reputation monitoring service, Domain Watch, which performs exactly what we will discuss in this article. While working at Soteria, I not only witnessed this service in action but also contributed to taking down countless malicious domains before they could impact our clients. Having seen this in action and the continuous improvements, as well as the relevance to what we'll be discussing, asking them to sponsor this article was a no-brainer.
Understanding Certificate Transparency Logs and Domain Registration Monitoring
One of the most common tactics every cybersecurity professional is familiar with is when threat actors abuse subdomains, domains, and URIs that closely resemble those of the target organization. They do this to deceive users and gain unauthorized access, making it easier to execute phishing attacks, distribute malware, and steal sensitive information. Even extremely seasoned security professionals can be tricked by techniques such as using non-ASCII characters that look similar to English characters. For instance, while apple.com might be legitimate, a malicious actor might use аpple.com (with a Cyrillic 'а' instead of a Latin 'a'), which is registered as xn--pple-43d.com, which is known as an IDN homograph attack..
Domain Monitoring
If you're reading this, you probably know what DNS is and how it works. However, just in case, DNS is a hierarchical and decentralized naming system that translates human-readable domain names (like www.example.com) into machine-readable IP addresses (like 192.0.2.1). DNS operates through a distributed database system comprising various types of DNS servers, including root servers, top-level domain (TLD) servers, and authoritative DNS servers.
DNS zone files are crucial components of this system, typically contained within authoritative DNS servers. These plain text files store mappings between domain names and IP addresses. They contain various DNS records, such as A, AAAA, CNAME, MX, and TXT records, which define the resources available under a domain. Each TLD has its own zone file, which is publicly accessible due to the nature of how DNS works. Services like DomainTools can help provide this information.
Certificate Transparency
I recommend checking out certificate.transparency.dev as it has an excellent write-up on how Certificate Transparency (CT) works. To summarize, CT is a system designed to enhance the security of the Web Public Key Infrastructure (Web PKI) by logging SSL/TLS certificates in publicly accessible, append-only logs. When a Certificate Authority (CA) issues a certificate, it submits a precertificate to one or more CT logs, receiving a Signed Certificate Timestamp (SCT) in return. This SCT is a promise that the certificate will be included in the log within a specified time, ensuring transparency and accountability. This allows companies to monitor for unauthorized or suspicious TLS certificates issued for domains similar to their own, helping to prevent threats from encrypted traffic used by malicious actors.
Examples in the Wild
For most of my readers, none of the information so far in this blog should be too shocking as it's just high-level information on how DNS and TLS transparency work. However, let's dig into some real examples of how a threat actor may target an organization in the wild and how powerful monitoring for new domains being registered to yours can be hugely impactful in starting to make your security program proactive vs reactive.
Scattered Spider
Scattered Spider is a sophisticated threat actor known for its aggressive social engineering attacks, even against organizations with strong security programs. Recently featured on 60 Minutes, Scattered Spider employs techniques like phishing, push bombing, and SIM swapping to compromise targets. They often impersonate IT and helpdesk staff to trick employees into revealing credentials or running remote access tools.
It's not uncommon for organizations to have various domains outside of their primary domain for different applications, which unfortunately has made tactics like this more effective. Scattered Spider, for example, per a recent CISA Advisory, has been known to abuse this by registering domains that seem legitimate to technical users they are targeting, such as victimname-sso[.]com, victimname-servicedesk[.]com, and victimname-okta[.]com.
Opportunists and Protecting Your Clients
Scammers often exploit crises and the accompanying sense of urgency. For example, the recent outage caused by CrowdStrike led to numerous domains being registered by threat actors looking to take advantage of the situation.
In their blog, CrowdStrike identified several domains targeting their customers impacted by the outage:
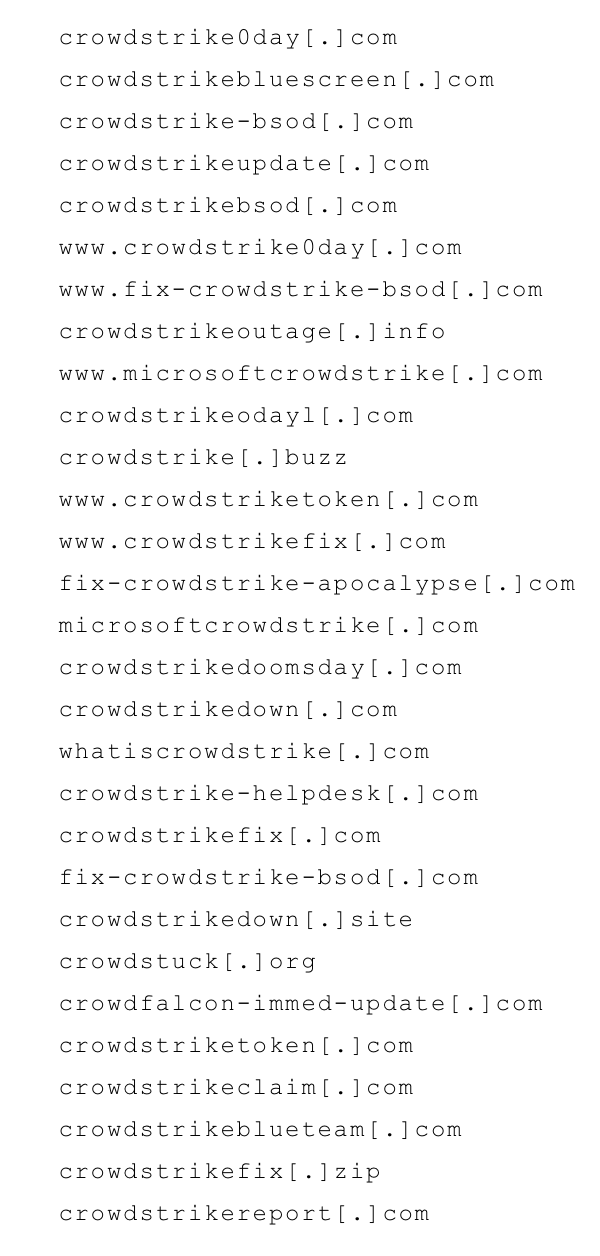
CrowdStrike isn't unique in this situation. It's important to remember that not every domain registered with your name will be used against you, but some may be used against your clients, as seen in CrowdStrike's case, or to blend in with them.
A notable example involves Google. In the polyfill supply chain attack, Google’s brand was abused by replacing lowercase ls with is in the malicious domain www[.]googie-anaiytics[.]com. The threat actor had registered the domain over a year before the polyfill attack was detected! Imagine if the threat actor had been hosting something more impactful than a spam redirector, or if the domain had been used in a major attack that made the news, the reptuational hit Google would have received. Especially with such an easy one to have detected.
By monitoring your domain, you not only raise the security posture of your organization but also make it much more difficult for threat actors to target your clients. This proactive measure is a significant win for your security efforts.
Malicious Registrations as an Early Warning System
Monitoring new domain registrations allows you to take down and block domains before they can be used against you and can also serve as an early warning system. For example, if your organization stays updated on CISA advisories and detects a domain like victimname-sso[.]com, it can indicate which threat actor may be targeting you. This knowledge allows your organization to take proactive measures, such as notifying targeted teams (e.g., the helpdesk) and giving them specific techniques to watch out for. You can also re-prioritize internal controls to prevent or detect the threat actor more effectively.
Free Alternatives to Paid Tools and Recommendations
If your organization can't or won't pay for a brand reputation monitoring service, don't worry—there are tools and methods you can use for basic monitoring.
dnstwist.py
Free tools like dnstwist.py check commonly abused permutations of your domain automatically. Running this regularly can help detect malicious domains:

Leveraging Existing Security Enrichment APIs
Many security monitoring programs already pay for tools that provide various enrichments, which may include an API for searching newly registered domains. Alternatively, free services like Certificate Transparency logs or ICANN offer similar information. When building your own solution, check for common permutations, character replacements, and words associated with your organization. For example, a university should include its name and possibly its mascot's name.
Proactively Buying Domain Names to Prevent Abuse
If possible, proactively purchasing domain names and variations of your domain can prevent them from falling under attacker control. Blocking domain permutations in your network won’t stop attackers from registering and targeting your clients or employees through channels outside your network control, such as social media or personal devices. By controlling the domain, you can prevent its malicious use. However, this strategy will not stop attackers from targeting you or prevent them from registering similar domains. Securing the most realistic and likely-to-be-abused variations, especially those with character substitutions, can force attackers to use less convincing domains that may be easier for your users to identify. While this approach can help, it is not a foolproof solution and should not be relied upon exclusively, as it can become a game of whack-a-mole.
Closing
As I mentioned earlier in this article, it is rare to find a security control that is relatively inexpensive and easy to implement while simultaneously providing such significant proactive prevention for both you and your customers. This control raises the overall cost for a threat actor targeting your organization, as they may have to switch up their TTPs or infrastructure, making your organization more difficult to attack. This kind of proactive measure can help push financially motivated threat actors to target other organizations in a "You don’t have to run faster than the bear to get away. You just have to run faster than the guy next to you.” sort of way.
Already have an account? Sign in
No spam, no sharing to third party. Only you and me.