Falling in love with NSM again
When I started in cybersecurity, most web traffic wasn’t encrypted, which meant Firewalls and Network Intrusion Detection Systems played a critical role in detecting malicious activity. Endpoint visibility was limited—most organizations still relied on traditional Anti-Virus solutions or, if they were ahead of the curve, Next-Gen Anti-Virus (NGAV). While NGAV improved detection capabilities, it often fell short when it came to providing the visibility needed for thorough investigations.
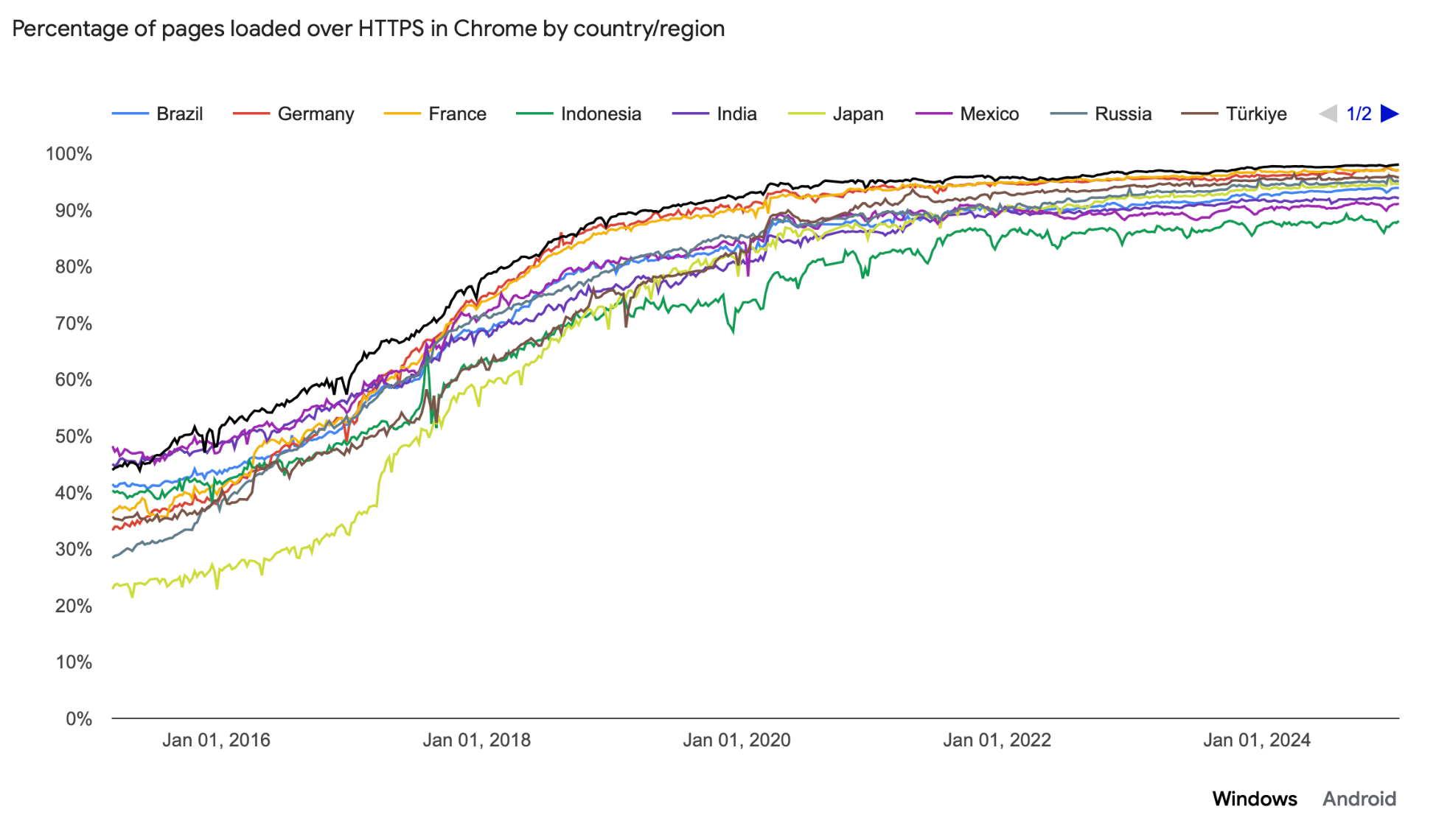
Figure 1: TLS Adoption Overtime by Google
Transparency: I currently work with the NDR company Corelight as a Security Researcher, however this was written on my own time and was not an ask from work, but a genuine post about NSM.
Host-level insights typically came from Windows Event Logs or Linux audit logs, but even if these logs were available, they rarely provided modern “flight recorder”-style data that captured process ancestry and system activity in a way that made analysis straightforward. Analysts were left to piece together events manually. Early Endpoint Detection and Response (EDR) tools offered a step forward by collecting and displaying this data, but they were far from refined. Out-of-the-box detection rules were sparse, and those that existed were often plagued by false positives.
As EDR tools matured and began integrating NGAV (or vice versa), and as out-of-the-box rulesets improved, adoption skyrocketed. Within a few years, it seemed as if most organizations had deployed an EDR solution. A single tool now covered the majority of infrastructure, streamlined forensic collection, and presented data in a way that made investigating attacks significantly easier. EDR became so effective that some organizations relied on it entirely, with adoption accelerating as the shift to remote work during COVID made endpoint visibility even more critical.
New “Managed Detection and Response” vendors quickly emerged, many offering only or primarily EDR-based services. At one point, I jokingly told a former colleague—now Chief Investigator for Binalyze, Lee Sult—something along the lines of, “Just give me an EDR and a tool like Velociraptor, and I’ve got all I need.” While meant as a joke, my preference for combining network and endpoint data aside, it reflected just how widespread that mindset had become.
We've Got an EDR Deployed... Now What?
As EDR deployments matured, organizations once again turned to network data to address visibility gaps. One of the primary findings in CISA's 2024 red team assessment highlighted the dangers of over-reliance on EDR:
Lesson Learned: The assessed organization had insufficient technical controls to prevent and detect malicious activity. The organization relied too heavily on host-based endpoint detection and response (EDR) solutions and did not implement sufficient network layer protections.
My experience in consulting echoed these findings. During red team engagements, attackers frequently compromised devices that either couldn’t run an EDR, were in a degraded state, or had EDR outright disabled with tools such as EDRSilencer.
In nearly every case, network data became both the detection point and the first source of investigation—even in environments with well-configured EDR deployments. When assessing the initial scope, the first step is typically checking which systems communicated with a suspicious IP or made a specific DNS query. However, this was often attempted within the EDR itself because many organizations lacked even basic netflow data.
NSM's Role in the Encrypted World
Corelight has an excellent whitepaper on encrypted network traffic analysis, but we can take this concept even further. For serious Network Security Monitoring (NSM), the industry gold standard is typically a combination of Zeek and Suricata. Nearly all major NSM and Network Detection and Response (NDR) solutions use these tools under the hood, and they are widely adopted in ICS/OT network monitoring as well.
When dealing with encrypted traffic, Zeek is particularly powerful. Among its many capabilities, it allows detection engineers to write custom scripts that extend its functionality. For example, Corelight recently developed a Sliver network detector that works even on encrypted traffic.
Beyond its scripting flexibility, Zeek's sheer volume of network metadata is invaluable. This level of detail enables organizations to establish comprehensive baselines—something that other tools in the space do not match. The ability to analyze this data is especially useful for both threat hunting and detection engineering. If you're familiar with the PEAK Threat Hunting Framework, you'll recognize how well Zeek's data supports its methodologies.
Hypothesis-Driven Hunts
Hypothesis-Driven hunts often begin with insights from threat intelligence. For example, TrendMicro’s 2021 report on SSL/TLS certificates revealed:
The signs of potential malicious activity start with how the certificates in question are signed. Of the certificates we examined, 60% were self-signed. This in itself should be a significant red flag. The name of the organization in the certificate itself frequently provides warning signs as well: some malware families like AsyncRAT and BitRAT include their own malware names in this field, while other malware families use some permutation of “default” or the oddly named “Internet Widgits Pty Ltd,” which is the default organization name used when OpenSSL creates certificates.
Zeek’s extensive metadata collection in its ssl.log and x509.log makes identifying this behavior straightforward. With these logs, analysts can efficiently query all self-signed certificate traffic within their environment, assess anomalies, and and easily determine legitimacy.
Model-Assisted Threat Hunts (M-ATH)
Model-Assisted Threat Hunts leverage statistical models and machine learning to detect abnormal behavior. As I've said a million times this blog post, Zeek’s metadata collection far surpasses that of other network monitoring tools, making it an ideal foundation for advanced statistical modeling. Its extensive set of fields and well-structured logs enable deep analysis of network traffic patterns.
There are third-party tools like ZAT (Zeek Analysis Tools) that extend Zeek’s capabilities, providing extensions and pre-built notebooks for analysis. However, most organizations take this a step further by integrating Zeek data into their SIEM and using custom Jupyter Notebooks and machine learning models.
Baseline Hunts
Baseline hunts are one of my favorite approaches to detection. At its core, baselining involves analyzing network activity and alerting on deviations from established norms. A simple example would be monitoring a server subnet and defining an alert condition: IF traffic from 10.0.1.1/24 appears on ANY ports OTHER than 53/80/443/8080, trigger an alert. The goal is to investigate any deviations and determine their cause. This method is highly effective, as it can make entire classes of attacks significantly more difficult - any reverse shell using an unexpected port, for instance, would immediately stand out.
For those more familiar with host-based detection, a comparable concept can be found in this Sigma Rule, which detects Microsoft Office products spawning suspicious child processes. The rule explicitly lists high-risk processes (powershell.exe, wmic.exe, etc.). A more robust method would involve profiling normal child processes spawned by Office applications in your specific environment and alerting on any deviations. This transforms a deny list approach into an allow list, making evasions far more challenging.
Returning to network-based detection, the destination port example is just one approach. You could also monitor for HTTP requests to commonly abused TLDs where the URI includes an .exe download. These methods significantly raise the bar for adversaries, making stealthy operations far more difficult.
Closing Thoughts
As organizations refine their security strategies, it's critical to assess whether there is an over-reliance on EDR—even in well-established deployments. Findings from CISA’s red team assessments and real-world incidents repeatedly underscore the importance of network telemetry in closing visibility gaps.
This isn’t about replacing EDR—it’s about strengthening it. Effective use of NSM provides an additional layer of detection, reduces blind spots, and enhances response capabilities before threats escalate. It should be noted, commercial offerings such as Corelight actually can integrate directly into some EDR/XDR tools.
As attackers evolve, defenders must adopt a more comprehensive approach—one that fully integrates network data as a fundamental component of modern security operations.
Already have an account? Sign in
No spam, no sharing to third party. Only you and me.