A Deep Dive into Linux Ransomware Research
Over the past few weeks, I have done a deep dive into the public research available on Linux Ransomware, seeking to understand the broader landscape as there is an over emphasis on the Mirai botnet. I discovered that although there is an abundance of outstanding whitepapers and research pieces, they are distributed across various blogs, making them challenging to assemble. Adding to the complexity, most samples are typically only accessible via a paid service like VirusTotal.
As a fellow community researcher, I recognized that there is a need to make this research more accessible, thus the write-up.
The journey to acquiring all the various samples accounted for a significant portion of the time spent on this blog, attesting to the very issue we're trying to address. In a field where community involvement is vital, it's unfortunate that these samples are often locked behind paid services. With this blog, I aim to challenge this dynamic and make these valuable resources more readily available to the public via accessible services such as those offered by abuse.ch.

This blog post is proudly sponsored by Sandfly Security. Visit their website at https://sandflysecurity.com/. It's not by accident that I approached Sandfly Security to sponsor this post; I firmly believe in their product and confidently endorse it as one of the market's premier Linux security monitoring tools.
In terms of detection capabilities for Linux, no existing EDR comes close to Sandfly. The amount of telemetry data Sandfly can pull far surpasses other competitors, and its ability to support virtually all known CPU architectures and Linux flavors, including rolling releases like Arch Linux, truly sets it apart.
For further insight into Sandfly's powerful capabilities, I invite you to explore a previous post I've written on the product: Leveling Up Your Linux Security Monitoring. The incident handlers over at SANS have also recently shared their thoughts on Sandfly: Sandfly Security by SANS.
Understanding Linux Ransomware and its Impact
The effects of a ransomware attack can be devastating. Beyond the direct financial cost of the ransom itself, victims often suffer significant data loss, downtime, and reputational damage. For businesses, this can result in loss of customer trust and potentially massive financial losses. For individuals, it can mean the loss of irreplaceable personal files and data.
Ransomware's primary job is to encrypt files on the targeted system, rendering them inaccessible to the user. Modern ransomware uses strong encryption algorithms, making it nearly impossible to recover the files without the unique decryption key held by the attacker.
Linux servers themselves make quite appealing targets for modern threat actors as they are typically what run critical operations within a business as well as databases containing some of the more sensitive organization secrets. Now that threat actors are also threatening to releasae the data if they are not paid (IE: maybe you have great backups and can recover), you can see why a Linux server may make a nice target.
Examining the Linux Ransomware Landscape
During my research, I quickly realized there are two major categories: those that target hypervisors and the related VM files, and more traditional forms that target the host server itself.
This is often a distinction that isn't made very clear, however it does have some major implications, namely when it comes to detecting and responding to the activity involved.
Hypervisors 101: Establishing Context for Ransomware Techniques
In the world of virtualization, hypervisors play an essential role. These act as the software, firmware, or hardware components that create and manage virtual machines (VMs) – or servers that share the same physical hardware. Depending on how they interface with the underlying system, hypervisors are often classified as Tier 1 or Tier 2.
Tier 1 Hypervisors
Also known as "bare-metal" hypervisors, Tier 1 hypervisors interact directly with the system hardware. They don't require an underlying operating system to function, instead effectively serving as the operating system for the server.
VMware's ESXi is a prime example of a Tier 1 hypervisor that is installed straight onto the server.
Tier 2 Hypervisors
In contrast, Tier 2 hypervisors, often referred to as "hosted" hypervisors, and they operate on top of an existing operating system, like any other software application. In this scenario, the underlying operating system is known as the "host," and the VMs' operating systems are referred to as "guests."
Oracle's VirtualBox is a well-known Tier 2 hypervisor that is commonly used on local systems for testing.
Hypervisor-Focused Attacks
A notable example of hypervisor-targeting ransomware is RedAlert. As I mentioned earlier, instead of executing a binary on the underlying virtual machines (Linux and Windows servers for example), RedAlert's crew attacks the hypervisor itself (VMWare eSXI). This matters because your Linux server logs/EDR type tooling will NOT be able to see this activity.
As BleepingComputer noted, the ransomware zeroes in on specific file types associated with VMware ESXi virtual machines: these include log files, swap files, virtual disks, and memory files, among others. When encrypting files, the ransomware appends the .crypt[number] extension to the file names of the encrypted files.
Targeted File Extensions
When encrypting files, the ransomware will only target files associated with VMware ESXi virtual machines, including log files, swap files, virtual disks, and memory files, as listed below.
.log
.vmdk
.vmem
.vswp
.vmsnIn the sample analyzed by BleepingComputer, the ransomware would encrypt these file types and append the .crypt[number] extension to the file names of encrypted files.
Source Data: BleepingComputer Article
Hypervisor Focused Families
- RedAlert (esxcli) SHA256: 039e1765de1cdec65ad5e49266ab794f8e5642adb0bdeb78d8c0b77e8b34ae09
- Conti SHA256: 8b57e96e90cd95fc2ba421204b482005fe41c28f506730b6148bcef8316a3201
- BlackBasta SHA256: 96339a7e87ffce6ced247feb9b4cb7c05b83ca315976a9522155bad726b8e5be
- Sodinokibi/REvil SHA256: a322b230a3451fd11dcfe72af4da1df07183d6aaf1ab9e062f0e6b14cf6d23cd
- BlackMatter/DarkSide SHA256: 6a7b7147fea63d77368c73cef205eb75d16ef209a246b05698358a28fd16e502
- Defray777/RansomEXX SHA256: cb408d45762a628872fa782109e8fcfc3a5bf456074b007de21e9331bb3c5849
- HelloKitty/ViceSociety SHA256: 556e5cb5e4e77678110961c8d9260a726a363e00bf8d278e5302cb4bfccc3eed
- Royal SHA256: b57e5f0c857e807a03770feb4d3aa254d2c4c8c8d9e08687796be30e2093286c
- BlackSuit SHA256: 1c849adcccad4643303297fb66bfe81c5536be39a87601d67664af1d14e02b9e
- RTM Locker SHA256: d68c99d7680bf6a4644770edfe338b8d0591dfe143278412d5ed62848ffc99e0
Detection Strategies
- Ensure your eSXI servers are logging to your SIEM, and alert on any
SSHattempt whether it passes or fails. HavingSSHenabled on the eSXI host is typically bad practice, however if you have to allow it, ensure the organization baselines what networks are the source of the traffic. - Alert on network traffic over port 22 either via network metadata in the SIEM or via a Network Intrusion Detection System (NIDS) such as SecurityOnion.
- If running SecurityOnion, taking advantage of Strelka to run YARA signatures across the files traversing the organization network.
Traditional Host Targeting
These you can think of that is more similar to a traditional Windows Ransomware binary that executes on the host where you may have some traditional visibility in place.
- Hive SHA256: 713b699c04f21000fca981e698e1046d4595f423bd5741d712fd7e0bc358c771
- GonnaCry SHA256: f5de75a6db591fe6bb6b656aa1dcfc8f7fe0686869c34192bfa4ec092554a4ac
- Erebus SHA256: 0b7996bca486575be15e68dba7cbd802b1e5f90436ba23f802da66292c8a055f
- eChOraix/QNAPCrypt SHA256: cc112184b17d65229ce20487d98a3751dceb3efbee7bf70929a35b66416ae248
- Cylance Ransomware SHA256: d1ba6260e2c6bf82be1d6815e19a1128aa0880f162a0691f667061c8fe8f1b2c
- Polaris SHA256: e29aa629bf492a087a17fa7ec0edb6be4b84c5c8b0798857939d8824fa91dbf9
Detection Strategies
One common disappointment in many technical write-ups about Linux-based malware, including ransomware, is the overemphasis and focus on reverse-engineering the malicious binary. This often overshadows crucial aspects such as how was the malware delivered? Once the binary was on disk, what method was used to execute the binary?
This was a big place of disappointment. That said as you'd probably guessed, most of the initial access that I was able to identify involved the exploitation of some sort of RCE of a service that is exposed to the internet. With this information we can form a few differing detection hypothesis:
- Exploiting an RCE of an application exposed to the internet will likely spawn some abnormal child processes. Identify the process names of your applications and their associated database processes and baseline which child processes are normal, and what the normal CLI arguments are. A detection to the tune of
parent.process:$APP_Processname | child.process:$Any_Process_Not_In_Normal_Baseline.This visibility is provided in the built in logging of Linux or through most modern 3rd party security monitoring tools. - The above detection method is likely also a good idea to apply to your webserver (
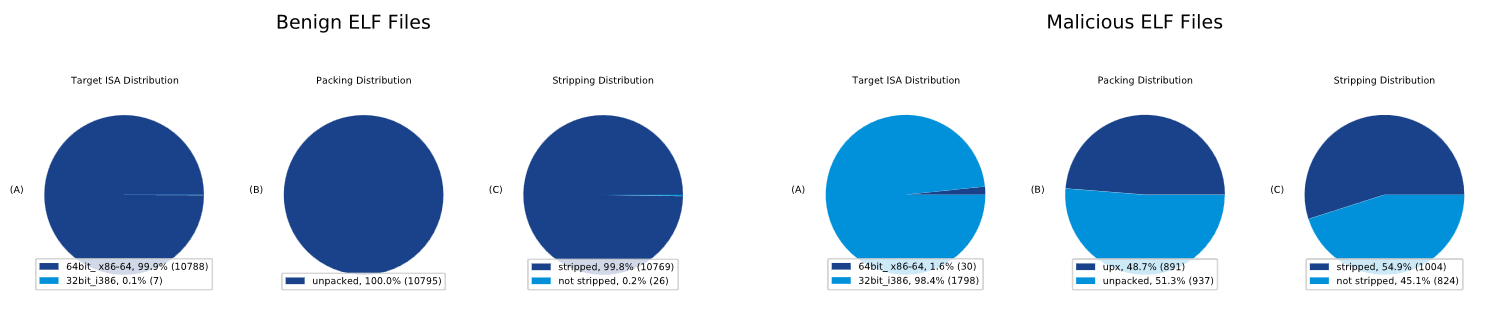
caddy,nginx,apache2,etc) for the same purpose. - VMWare put out a wonderful set of research around Linux malware that confirmed something I've always had a hunch was true, but never had data to actually back the claim up, in that MOST legitimate Linux software is unpacked, which should make any packed binary executing on a linux server in your environment worth looking at and alerting on. You can identify this through tooling that may capture a binaries entropy, or through the use of YARA rules identifying packed
ELFbinaries that contain packers likeUPX
Conclusion
Ultimately digging into Linux Ransomware was illuminating. The state of linux malware research has such a heavy emphasis on Coinminers that I was honestly surprised with the amount of Ransomware out there that impacts Linux. It was also surprising to see that most of the research I found identified Ransomware targeting Linux appears to be primarily around attacking the Linux VM's at the HyperVisor level making it essentially invisible to your EDR tooling and logging alone - which I think would be a surprise to many. A key takeaway I recommend - send your hypervisor logs to your SIEM and build those detectors!!!
YARA Signatures
Here are a list of YARA signatures I was able to identify and find for the Ransomware discussed in this article:
Generic eSXI based Ransomware
**https://github.com/signalblur/detection-artifacts/blob/main/yara/linux_malware.yar**
rule eSXI_Ransomware {
meta:
description = "linux_ransomware - file DarkSide_BlackMatter"
author = "signalblur"
reference = "Linux Research"
date = "2023-07-17"
DarkSide_BlackMatter_hash1 = "6a7b7147fea63d77368c73cef205eb75d16ef209a246b05698358a28fd16e502"
HelloKitty_hash2 = "556e5cb5e4e77678110961c8d9260a726a363e00bf8d278e5302cb4bfccc3eed"
Conti_hash3 = "8b57e96e90cd95fc2ba421204b482005fe41c28f506730b6148bcef8316a3201"
strings:
$a1 = "Unable To Get Process List" ascii
$a2 = "app::esxi_utils::get_process_list" ascii
$a3 = "app::master_proc::process_file_encryption" ascii
$a4 = "app::file_encrypter::process_file" ascii
$a5 = "execvp failure" ascii
$e1 = "esxcli vm process kill" ascii
$e2 = "esxcli vm process list" ascii
$e3 = "esxcli --formatter=csv" ascii
$e4 = "error encrypt: %s rename back:%s" fullword ascii
$e5 = "vm process kill --type=force" ascii
$r1 = "Download TOR Browser" ascii
$r2 = "We offer you to purchase special decryption software" ascii
$r3 = "Using silent mode, if you on esxi - stop VMs manualy" fullword ascii
$r4 = "File [%s] was encrypted" fullword ascii
$r5 = "File [%s] was NOT encrypted" fullword ascii
$r6 = " without --path encrypts current dir" fullword ascii
$r7 = "All of your files are currently encrypted by CONTI strain" ascii
$r8 = "DON'T TRY TO IGNORE" ascii
$r9 = "DONT'T TRY TO RECOVER" ascii
condition:
uint16(0) == 0x457f and filesize < 6000KB and
2 of them
}
RedAlert
**https://github.com/signalblur/detection-artifacts/blob/main/yara/linux_malware.yar**
rule RedAlert {
meta:
description = "linux_ransomware - file RedAlert"
author = "signalblur"
reference = "Linux Research"
date = "2023-07-17"
hash1 = "039e1765de1cdec65ad5e49266ab794f8e5642adb0bdeb78d8c0b77e8b34ae09"
strings:
$s1 = "esxcli --formatter=csv" ascii
$s2 = "vm process list | tail -n +2" ascii
$s3 = "Run command for stop all running VM`s." fullword ascii
$s4 = "vm process kill" fullword ascii
$s5 = "# ATTENTION the argument given first will be used for target(file or path)" fullword ascii
$s6 = "search and encryption will include subdirectories" ascii
$s9 = "Download TOR Browser" ascii
$s10 = "[info] Execution time check: %f" fullword ascii
$s11 = "Encryption is reverssible process" ascii
$s15 = "Run command for stop all running VM`s" ascii
$s16 = "[info] File: %s/%s, begin encryption" fullword ascii
$s17 = "Don't modify contents of the encrypted files" ascii
$s18 = "We offer you to purchase special decryption software, payment includes decryptor, key for it and erasure of stolen data" fullword ascii
$s19 = "DumpHex" fullword ascii
$s20 = "On our webpage you will be able to purchase decryptor, chat with our support and decrypt few files for free" fullword ascii
condition:
uint16(0) == 0x457f and filesize < 1000KB and
5 of them
}
**https://github.com/reversinglabs/reversinglabs-yara-rules/blob/develop/yara/ransomware/Linux.Ransomware.RedAlert.yara**
rule Linux_Ransomware_RedAlert : tc_detection malicious
{
meta:
author = "ReversingLabs"
source = "ReversingLabs"
status = "RELEASED"
sharing = "TLP:WHITE"
category = "MALWARE"
malware = "REDALERT"
description = "Yara rule that detects RedAlert ransomware."
tc_detection_type = "Ransomware"
tc_detection_name = "RedAlert"
tc_detection_factor = 5
strings:
$encrypt_files_p1 = {
41 57 41 56 41 55 41 54 55 53 48 81 EC ?? ?? ?? ?? 48 89 74 24 ?? BE ?? ?? ?? ?? 48
89 54 24 ?? 48 89 4C 24 ?? 4C 89 44 24 ?? E8 ?? ?? ?? ?? 48 85 C0 48 89 C5 75 ?? BF
?? ?? ?? ?? E8 ?? ?? ?? ?? EB ?? 48 89 C7 E8 ?? ?? ?? ?? 83 F8 ?? 89 C3 75 ?? BF ??
?? ?? ?? E8 ?? ?? ?? ?? 48 89 EF E8 ?? ?? ?? ?? 31 C0 E9 ?? ?? ?? ?? 48 8D 54 24 ??
89 C6 BF ?? ?? ?? ?? E8 ?? ?? ?? ?? FF C0 75 ?? BF ?? ?? ?? ?? EB ?? 4C 8B B4 24 ??
?? ?? ?? 4D 85 F6 7F ?? BF ?? ?? ?? ?? E8 ?? ?? ?? ?? 89 DF E8 ?? ?? ?? ?? EB ?? 49
81 FE ?? ?? ?? ?? C7 44 24 ?? ?? ?? ?? ?? 0F 97 44 24 ?? 49 81 FE ?? ?? ?? ?? 0F 97
44 24 ?? 80 7C 24 ?? ?? 74 ?? BA ?? ?? ?? ?? 4C 89 F0 C7 44 24 ?? ?? ?? ?? ?? 48 89
D3 31 D2 48 F7 F3 48 6B C8 ?? 48 89 4C 24 ?? 49 81 FE ?? ?? ?? ?? 77 ?? 4D 89 F4 41
BD ?? ?? ?? ?? C7 44 24 ?? ?? ?? ?? ?? EB ?? 41 BC ?? ?? ?? ?? 45 31 ED C7 44 24 ??
?? ?? ?? ?? 4D 63 FD C7 44 24 ?? ?? ?? ?? ?? 4C 0F AF 7C 24 ?? E9 ?? ?? ?? ?? 80 7C
24 ?? ?? 74 ?? 45 85 ED 74 ?? 80 7C 24 ?? ?? 74 ?? 41 8D 45 ?? 3B 44 24 ?? 4C 89 FE
75 ?? 49 8D B6 ?? ?? ?? ?? EB ?? 31 F6 31 D2 48 89 EF E8 ?? ?? ?? ?? 48 63 7C 24 ??
48 89 E9 4C 89 E2 48 03 7C 24 ?? BE ?? ?? ?? ?? E8 ?? ?? ?? ?? 4C 39 E0 74 ?? BF ??
?? ?? ?? EB ?? 44 01 64 24 ?? 41 FF C5 44 3B 6C 24 ?? 0F 85 ?? ?? ?? ?? 48 8D 9C 24
?? ?? ?? ?? BA ?? ?? ?? ?? BE ?? ?? ?? ?? 48 89 DF E8 ?? ?? ?? ?? 84 C0 74 ?? BF ??
?? ?? ?? EB ?? 48 8D BC 24 ?? ?? ?? ?? BA ?? ?? ?? ?? 48 89 DE E8 ?? ?? ?? ?? 85 C0
74 ?? BF ?? ?? ?? ?? E8 ?? ?? ?? ?? 4C 63 6C 24 ?? 45 89 E7 44 89 64 24 ?? 4C 0F AF
6C 24 ?? C6 44 24 ?? ?? C7 44 24 ?? ?? ?? ?? ?? E9 ?? ?? ?? ?? 4C 8B 4C 24 ?? 41 B8
?? ?? ?? ?? B9 ?? ?? ?? ?? BA ?? ?? ?? ?? BE ?? ?? ?? ?? 48 89 DF E8 ?? ?? ?? ?? 84
}
$encrypt_files_p2 = {
C0 75 ?? 48 8B 54 24 ?? 48 8B 7C 24 ?? 48 89 E9 BE ?? ?? ?? ?? E8 ?? ?? ?? ?? 0F B7
15 ?? ?? ?? ?? 48 39 D0 75 ?? 48 8B 44 24 ?? 48 89 E9 BE ?? ?? ?? ?? 0F B7 50 ?? 48
8B 38 E8 ?? ?? ?? ?? 48 8B 4C 24 ?? 0F B7 51 ?? 48 39 D0 74 ?? BF ?? ?? ?? ?? E9 ??
?? ?? ?? 48 89 EF E8 ?? ?? ?? ?? 4C 03 7C 24 ?? 44 3B 6C 24 ?? 0F 8C ?? ?? ?? ?? E9
?? ?? ?? ?? BF ?? ?? ?? ?? EB ?? BF ?? ?? ?? ?? E8 ?? ?? ?? ?? E9 ?? ?? ?? ?? 80 7C
24 ?? ?? 74 ?? 83 7C 24 ?? ?? 74 ?? 80 7C 24 ?? ?? 74 ?? 8B 44 24 ?? 4C 89 EE FF C0
3B 44 24 ?? 75 ?? 49 8D B6 ?? ?? ?? ?? EB ?? 31 F6 31 D2 48 89 EF E8 ?? ?? ?? ?? 48
63 44 24 ?? 48 8B 5C 24 ?? 48 8D B4 24 ?? ?? ?? ?? 48 8D BC 24 ?? ?? ?? ?? 31 C9 31
D2 45 89 E1 C7 44 24 ?? ?? ?? ?? ?? C7 44 24 ?? ?? ?? ?? ?? 48 01 C3 48 8D 84 24 ??
?? ?? ?? 49 89 D8 48 89 1C 24 48 89 44 24 ?? E8 ?? ?? ?? ?? 85 C0 0F 85 ?? ?? ?? ??
48 89 E9 4C 89 E2 BE ?? ?? ?? ?? 48 89 DF E8 ?? ?? ?? ?? 4C 39 E0 0F 85 ?? ?? ?? ??
FF 44 24 ?? 8B 54 24 ?? 8B 4C 24 ?? 01 54 24 ?? 39 4C 24 ?? 75 ?? 31 F6 BA ?? ?? ??
?? 48 89 EF E8 ?? ?? ?? ?? 48 8D BC 24 ?? ?? ?? ?? 48 89 E9 BA ?? ?? ?? ?? BE ?? ??
?? ?? E8 ?? ?? ?? ?? 8A 5C 24 ?? 48 83 F8 ?? B0 ?? 0F 44 D8 44 3B 7C 24 ?? 88 5C 24
?? 74 ?? BF ?? ?? ?? ?? E8 ?? ?? ?? ?? 44 03 7C 24 ?? 4C 03 6C 24 ?? 8B 44 24 ?? 39
44 24 ?? 0F 8C ?? ?? ?? ?? 48 89 EF E8 ?? ?? ?? ?? 0F B6 44 24 ?? 48 81 C4 ?? ?? ??
?? 5B 5D 41 5C 41 5D 41 5E 41 5F C3
}
$find_files_p1 = {
41 57 FC 41 56 41 55 41 54 49 89 FC 55 53 48 83 EC ?? 48 8B 84 24 ?? ?? ?? ?? 48 89
4C 24 ?? 48 83 C9 ?? 48 89 74 24 ?? 4C 89 44 24 ?? 4C 89 4C 24 ?? 88 54 24 ?? 48 89
44 24 ?? 48 8B 84 24 ?? ?? ?? ?? 44 8A BC 24 ?? ?? ?? ?? 48 89 44 24 ?? 48 8B 84 24
?? ?? ?? ?? 48 89 44 24 ?? 48 8B 84 24 ?? ?? ?? ?? 48 89 44 24 ?? 31 C0 F2 AE 4C 89
E7 48 F7 D1 4C 8D 71 ?? E8 ?? ?? ?? ?? 48 85 C0 48 89 44 24 ?? 0F 85 ?? ?? ?? ?? E8
?? ?? ?? ?? 8B 38 E8 ?? ?? ?? ?? 48 83 C4 ?? 4C 89 E6 48 89 C2 5B 5D 41 5C 41 5D 41
5E 41 5F BF ?? ?? ?? ?? 31 C0 E9 ?? ?? ?? ?? 45 84 FF 48 8D 6B ?? 74 ?? 0F B6 4B ??
48 89 EA 4C 89 E6 BF ?? ?? ?? ?? 31 C0 E8 ?? ?? ?? ?? 80 7B ?? ?? 0F 85 ?? ?? ?? ??
80 7C 24 ?? ?? 0F 84 ?? ?? ?? ?? BE ?? ?? ?? ?? 48 89 EF E8 ?? ?? ?? ?? 85 C0 0F 84
?? ?? ?? ?? BE ?? ?? ?? ?? 48 89 EF E8 ?? ?? ?? ?? 85 C0 0F 84 ?? ?? ?? ?? BE ?? ??
?? ?? 48 89 EF E8 ?? ?? ?? ?? 85 C0 0F 84 ?? ?? ?? ?? FC 31 C0 48 83 C9 ?? 48 89 EF
F2 AE 4C 89 F0 48 29 C8 48 3B 44 24 ?? 76 ?? 48 8B 3D ?? ?? ?? ?? 48 89 E9 4C 89 E2
BE ?? ?? ?? ?? 31 C0 E8 ?? ?? ?? ?? E9 ?? ?? ?? ?? 4B 8D 1C 34 48 89 EE 48 8D 7B ??
C6 03 ?? E8 ?? ?? ?? ?? 41 0F B6 C7 4C 8B 4C 24 ?? 4C 8B 44 24 ?? 89 44 24 ?? 48 8B
44 24 ?? BA ?? ?? ?? ?? 48 8B 4C 24 ?? 48 8B 74 24 ?? 4C 89 E7 48 89 44 24 ?? 48 8B
}
$find_files_p2 = {
44 24 ?? 48 89 44 24 ?? 48 8B 44 24 ?? 48 89 44 24 ?? 48 8B 44 24 ?? 48 89 04 24 E8
?? ?? ?? ?? E9 ?? ?? ?? ?? 45 84 FF 0F 85 ?? ?? ?? ?? FC 48 83 C9 ?? 48 89 EF 44 88
F8 F2 AE 48 8B 54 24 ?? 48 89 EF 48 89 CB 48 8B 4C 24 ?? 48 F7 D3 48 89 DE 4C 8D 6B
?? E8 ?? ?? ?? ?? 84 C0 74 ?? 48 89 EA 4C 89 E6 BF ?? ?? ?? ?? 31 C0 E8 ?? ?? ?? ??
E9 ?? ?? ?? ?? 4C 89 EA BE ?? ?? ?? ?? 48 89 EF E8 ?? ?? ?? ?? 85 C0 0F 84 ?? ?? ??
?? 48 89 DE 48 89 EF E8 ?? ?? ?? ?? 84 C0 0F 84 ?? ?? ?? ?? 4B 8D 1C 34 48 89 EA 4C
89 E6 BF ?? ?? ?? ?? 31 C0 E8 ?? ?? ?? ?? 48 8D 7B ?? 48 89 EE C6 03 ?? E8 ?? ?? ??
?? 0F B7 0D ?? ?? ?? ?? 4C 89 E7 4C 8B 44 24 ?? 48 8B 54 24 ?? 48 8B 74 24 ?? FF 15
?? ?? ?? ?? 84 C0 BF ?? ?? ?? ?? 74 ?? 48 8B 7C 24 ?? B9 ?? ?? ?? ?? 4C 89 E2 BE ??
?? ?? ?? 31 C0 E8 ?? ?? ?? ?? 48 8B 74 24 ?? 4C 89 E7 E8 ?? ?? ?? ?? 85 C0 74 ?? BF
?? ?? ?? ?? E8 ?? ?? ?? ?? BF ?? ?? ?? ?? E8 ?? ?? ?? ?? 48 8B 7C 24 ?? 41 8D 56 ??
4C 89 E6 E8 ?? ?? ?? ?? C6 03 ?? 48 8B 7C 24 ?? E8 ?? ?? ?? ?? 48 85 C0 48 89 C3 0F
85 ?? ?? ?? ?? 48 8B 7C 24 ?? 48 83 C4 ?? 5B 5D 41 5C 41 5D 41 5E 41 5F E9
}
$setup_environment = {
55 48 89 E5 41 56 49 89 F6 BE ?? ?? ?? ?? 41 55 41 54 53 48 89 FB 48 83 EC ?? E8 ??
?? ?? ?? 48 85 C0 49 89 C4 75 ?? BF ?? ?? ?? ?? E8 ?? ?? ?? ?? 48 8D 7D ?? E8 ?? ??
?? ?? 84 C0 BF ?? ?? ?? ?? 74 ?? BE ?? ?? ?? ?? 48 89 DF E8 ?? ?? ?? ?? 48 85 C0 49
89 C4 74 ?? 0F B7 55 ?? 48 8B 7D ?? 48 89 C1 BE ?? ?? ?? ?? E8 ?? ?? ?? ?? 0F B7 55
?? 48 8B 7D ?? 4C 89 E1 BE ?? ?? ?? ?? E8 ?? ?? ?? ?? 0F B7 55 ?? 31 C9 39 C2 0F 85
?? ?? ?? ?? E9 ?? ?? ?? ?? BF ?? ?? ?? ?? E8 ?? ?? ?? ?? E9 ?? ?? ?? ?? BF ?? ?? ??
?? 49 89 E5 E8 ?? ?? ?? ?? 66 8B 3D ?? ?? 22 00 66 03 3D ?? ?? 22 00 66 8B 05 ?? ??
22 00 66 89 7D ?? 0F B7 FF 66 89 45 ?? E8 ?? ?? ?? ?? 0F B7 7D ?? 48 89 45 ?? E8 ??
?? ?? ?? 0F B7 55 ?? 48 8B 7D ?? 4C 89 E1 BE ?? ?? ?? ?? 48 89 45 ?? E8 ?? ?? ?? ??
0F B7 55 ?? 48 8B 7D ?? 4C 89 E1 BE ?? ?? ?? ?? E8 ?? ?? ?? ?? 48 8B 75 ?? BF ?? ??
?? ?? 31 C0 E8 ?? ?? ?? ?? 0F B7 45 ?? 0F B7 35 ?? ?? ?? ?? 31 C9 48 8B 7D ?? 48 83
C0 ?? 25 ?? ?? ?? ?? 48 29 C4 48 8D 5C 24 ?? 48 83 E3 ?? 48 89 DA E8 ?? ?? ?? ?? 48
89 DE BF ?? ?? ?? ?? 31 C0 E8 ?? ?? ?? ?? 0F B7 3D ?? ?? ?? ?? BE ?? ?? ?? ?? 48 03
7D ?? E8 ?? ?? ?? ?? 66 39 05 ?? ?? 22 00 74 ?? BF ?? ?? ?? ?? E8 ?? ?? ?? ?? 4C 89
EC 31 C9 EB ?? 4C 89 E7 E8 ?? ?? ?? ?? 48 8D 75 ?? B9 ?? ?? ?? ?? 4C 89 F7 FC F3 A5
B1 ?? EB ?? 4C 89 EC EB ?? 48 8D 65 ?? 89 C8 5B 41 5C 41 5D 41 5E C9 C3
}
$make_configuration = {
41 56 BE ?? ?? ?? ?? 49 89 FE BF ?? ?? ?? ?? 41 55 41 54 55 53 48 83 EC ?? E8 ?? ??
?? ?? 84 C0 88 C3 74 ?? BF ?? ?? ?? ?? E8 ?? ?? ?? ?? 31 FF EB ?? BF ?? ?? ?? ?? E8
?? ?? ?? ?? BA ?? ?? ?? ?? 0F B7 F0 BF ?? ?? ?? ?? E8 ?? ?? ?? ?? BF ?? ?? ?? ?? E8
?? ?? ?? ?? B9 ?? ?? ?? ?? 49 89 C4 48 89 C2 BE ?? ?? ?? ?? BF ?? ?? ?? ?? 66 C7 00
?? ?? C6 40 ?? ?? E8 ?? ?? ?? ?? 4C 89 E6 BF ?? ?? ?? ?? 31 C0 E8 ?? ?? ?? ?? 48 89
E6 4C 89 E7 E8 ?? ?? ?? ?? 84 C0 75 ?? BF ?? ?? ?? ?? E8 ?? ?? ?? ?? BF ?? ?? ?? ??
E8 ?? ?? ?? ?? FC 88 D8 BF ?? ?? ?? ?? 48 83 C9 ?? F2 AE 48 F7 D1 48 FF C9 8D 59 ??
83 C1 ?? 48 63 F9 E8 ?? ?? ?? ?? 48 85 C0 48 89 C5 0F 84 ?? ?? ?? ?? 48 8D 78 ?? 48
63 D3 BE ?? ?? ?? ?? C6 00 ?? E8 ?? ?? ?? ?? 48 89 EF BE ?? ?? ?? ?? E8 ?? ?? ?? ??
48 85 C0 48 89 C3 BF ?? ?? ?? ?? 74 ?? 0F B7 54 24 ?? 48 8B 7C 24 ?? 48 89 C1 BE ??
?? ?? ?? E8 ?? ?? ?? ?? 48 89 DF E8 ?? ?? ?? ?? 48 89 EF E8 ?? ?? ?? ?? BF ?? ?? ??
?? E8 ?? ?? ?? ?? 4C 89 E7 E8 ?? ?? ?? ?? 4C 89 F7 48 89 E6 B9 ?? ?? ?? ?? FC F3 A5
48 83 C4 ?? 5B 5D 41 5C 41 5D 41 5E C3 BF ?? ?? ?? ?? E8 ?? ?? ?? ?? E9
}
condition:
uint32(0) == 0x464C457F and
(
$setup_environment
) and
(
all of ($find_files_p*)
) and
(
all of ($encrypt_files_p*)
) and
(
$make_configuration
)
}
**https://github.com/elastic/protections-artifacts/blob/main/yara/rules/Linux_Ransomware_RedAlert.yar**
rule Linux_Ransomware_RedAlert_39642d52 {
meta:
author = "Elastic Security"
id = "39642d52-0a4b-48d5-bb62-8f37beb4dc6a"
fingerprint = "744524ee2ae9e3e232f15b0576cdab836ac0fe3c9925eab66ed8c6b0be3f23d7"
creation_date = "2022-07-06"
last_modified = "2022-08-16"
threat_name = "Linux.Ransomware.RedAlert"
reference_sample = "039e1765de1cdec65ad5e49266ab794f8e5642adb0bdeb78d8c0b77e8b34ae09"
severity = 100
arch_context = "x86"
scan_context = "file, memory"
license = "Elastic License v2"
os = "linux"
strings:
$str_ransomnote = "\\%\\%\\%\\%\\%\\%\\%\\%\\%\\%\\%\\%\\%\\%\\% REDALERT UNIQUE IDENTIFIER START \\%\\%\\%\\%\\%\\%\\%\\%\\%\\%\\%\\%\\%\\%\\%" ascii fullword
$str_print = "\t\t\t########\n\t\t\t[ N13V ]\n\t\t\t########\n\n" ascii fullword
$str_arg = "[info] Catch -t argument. Check encryption time" ascii fullword
$str_ext = ".crypt658" ascii fullword
$byte_checkvm = { 48 8B 14 DD ?? ?? ?? ?? 31 C0 48 83 C9 FF FC 48 89 EE 48 89 D7 F2 AE 4C 89 E7 48 F7 D1 E8 }
condition:
3 of ($str_*) or ($byte_checkvm and $str_print)
}
Conti
**https://github.com/elastic/protections-artifacts/blob/main/yara/rules/Linux_Ransomware_Conti.yar**
rule Linux_Ransomware_Conti_53a640f4 {
meta:
author = "Elastic Security"
id = "53a640f4-905c-4b0d-ac4a-9ffdffd74253"
fingerprint = "d81309f83494b0635444234c514fda0edc05a11ac861c769a007f9f558def148"
creation_date = "2022-09-22"
last_modified = "2022-10-18"
threat_name = "Linux.Ransomware.Conti"
reference_sample = "8b57e96e90cd95fc2ba421204b482005fe41c28f506730b6148bcef8316a3201"
severity = 100
arch_context = "x86"
scan_context = "file, memory"
license = "Elastic License v2"
os = "linux"
strings:
$a = { 48 D3 EA 48 89 D0 83 E0 01 48 85 C0 0F 95 C0 84 C0 74 0B 8B }
condition:
all of them
}
**https://www.trellix.com/en-us/about/newsroom/stories/research/conti-group-targets-esxi-hypervisors-with-its-linux-variant.html**
rule RANSOM_Conti_Linux_Apr2022 : ransomware
{
meta:
description = "Detects Conti Linux variant"
author = "Marc Elias | Trellix ATR Team"
date = "2022-04-06"
strings:
$str1 = ".conti" ascii fullword
$str2 = "All of your files are currently encrypted by CONTI strain" ascii fullword
$str3 = "http://contirec" ascii
condition:
uint32(0) == 0x464c457f and
filesize < 2MB and
all of them
}
**https://github.com/signalblur/detection-artifacts/blob/main/yara/linux_malware.yar**
rule Conti {
meta:
description = "linux_ransomware - file Conti"
author = "signalblur"
reference = "Linux Research"
date = "2023-07-17"
hash1 = "8b57e96e90cd95fc2ba421204b482005fe41c28f506730b6148bcef8316a3201"
strings:
$s1 = "Something went wrong! - InitializeEncryptor " fullword ascii
$s2 = "Something went wrong! - RSA_public_encrypt!" fullword ascii
$s3 = "Process with PID %d was killed" fullword ascii
$s4 = "./locker --path /path" ascii
$s5 = "To prove that we REALLY CAN get your data back" ascii
$s6 = "Starting encryption - CONTI POC" ascii
$s9 = "All of your files are currently encrypted" ascii
$s11 = "download and install TOR browser" ascii
$s12 = "DON'T TRY TO IGNORE us" ascii
$s13 = "DONT'T TRY TO RECOVER" ascii
condition:
uint16(0) == 0x457f and filesize < 100KB and
4 of them
}
BlackBasta
**https://github.com/elastic/protections-artifacts/blob/main/yara/rules/Linux_Ransomware_BlackBasta.yar**
rule Linux_Ransomware_BlackBasta_96eb3f20 {
meta:
author = "Elastic Security"
id = "96eb3f20-9c40-4d40-8a6c-568a51c52d4d"
fingerprint = "5146ad9def7ccaba4b4896f345b0950c587ad5f96a106ec461caeb028d809ead"
creation_date = "2022-08-06"
last_modified = "2022-08-16"
threat_name = "Linux.Ransomware.BlackBasta"
reference_sample = "96339a7e87ffce6ced247feb9b4cb7c05b83ca315976a9522155bad726b8e5be"
severity = 100
arch_context = "x86"
scan_context = "file, memory"
license = "Elastic License v2"
os = "linux"
strings:
$a1 = "Done time: %.4f seconds, encrypted: %.4f gb" ascii fullword
$a2 = "Your data are stolen and encrypted" ascii fullword
$a3 = "fileEncryptionPercent" ascii fullword
$a4 = "fileQueueLocker" ascii fullword
$a5 = "totalBytesEncrypted" ascii fullword
$seq_encrypt_block = { 41 56 31 D2 41 55 41 54 49 89 FE 55 53 48 89 F5 49 63 D8 4C }
$seq_encrypt_thread = { 4C 8B 74 24 ?? 31 DB 45 31 FF 4D 8B 6E ?? 49 83 FD ?? 0F 87 ?? ?? ?? ?? 31 C0 4D 39 EF 0F 82 ?? ?? ?? ?? 48 01 C3 4C 39 EB 0F 83 ?? ?? ?? ?? }
condition:
3 of ($a*) and 1 of ($seq*)
}
Sodinokibi | REVil
**https://github.com/signalblur/detection-artifacts/blob/main/yara/linux_malware.yar**
rule Sodinokibi {
meta:
description = "linux_ransomware - file Sodinokib"
author = "signalblur"
reference = "Linux Research"
date = "2023-07-17"
hash1 = "a322b230a3451fd11dcfe72af4da1df07183d6aaf1ab9e062f0e6b14cf6d23cd"
strings:
$s1 = "Usage example: elf.exe --path /vmfs/ --threads 5 " fullword ascii
$s2 = "uname -a && echo \" | \" && hostname" fullword ascii
$s3 = "esxcli --formatter=csv" ascii
$s4 = "vm process list | awk -F" ascii
$s5 = "!!!BY DEFAULT THIS SOFTWARE USES 50 THREADS!!!" fullword ascii
$s6 = "[%s] already encrypted" fullword ascii
$s7 = "%d:%d: Comment not allowed here" fullword ascii
$s11 = "without --path encrypts current dir" ascii
$s17 = "File [%s] was NOT encrypted" fullword ascii
$s19 = "Using silent mode, if you on esxi - stop VMs manualy" ascii
$s20 = "File [%s] was encrypted" fullword ascii
condition:
uint16(0) == 0x457f and filesize < 300KB and
4 of them
}
**https://github.com/elastic/protections-artifacts/blob/main/yara/rules/Linux_Ransomware_Sodinokibi.yar**
rule Linux_Ransomware_Sodinokibi_2883d7cd {
meta:
author = "Elastic Security"
id = "2883d7cd-fd3b-47a5-9283-a40335172c62"
fingerprint = "d6570a8e9358cef95388a72b2e7f747ee5092620c4f92a4b4e6c1bb277e1cb36"
creation_date = "2022-01-05"
last_modified = "2022-01-26"
threat_name = "Linux.Ransomware.Sodinokibi"
reference_sample = "a322b230a3451fd11dcfe72af4da1df07183d6aaf1ab9e062f0e6b14cf6d23cd"
severity = 100
arch_context = "x86"
scan_context = "file, memory"
license = "Elastic License v2"
os = "linux"
strings:
$a = { 85 08 FF FF FF 48 01 85 28 FF FF FF 48 8B 85 08 FF FF FF 48 29 85 20 FF }
condition:
all of them
}
**https://cybersecurity.att.com/blogs/labs-research/revils-new-linux-version**
rule REvilLinux
{
meta:
author = "AlienLabs"
description = "REvil Linux"
sha256 = "ea1872b2835128e3cb49a0bc27e4727ca33c4e6eba1e80422db19b505f965bc4"
strings:
$func = "File [%s] was NOT encrypted"
$sleep = "esxcli"
$re = "[%s] is protected by os"
$a3 = "Error create note in dir %s"
condition:
uint32(0) == 0x464C457F and 3 of them
}
BlackMatter | DarkSide
**https://github.com/signalblur/detection-artifacts/blob/main/yara/linux_malware.yar**
rule DarkSide_BlackMatter {
meta:
description = "linux_ransomware - file DarkSide_BlackMatter"
author = "signalblur"
reference = "Linux Research"
date = "2023-07-17"
hash1 = "6a7b7147fea63d77368c73cef205eb75d16ef209a246b05698358a28fd16e502"
strings:
$s1 = "Unable To Get Process List, " ascii
$s2 = "app::esxi_utils::get_process_list" ascii
$s3 = "app::master_proc::process_file_encryption" ascii
$s4 = "app::file_encrypter::process_file" ascii
$s5 = "execvp failure" ascii
condition:
uint16(0) == 0x457f and filesize < 6000KB and
3 of them
}
**https://www.recordedfuture.com/blackmatter-ransomware-protection**
rule MAL_BlackMatter_Linux
{
meta:
author = “LKAYE, Insikt Group, Recorded Future”
date = “2021-07-28”
description = “Rule to detect BlackMatter ransomware Linux payload”
version = “1.0”
RF_MALWARE = “BlackMatter Ransomware”
strings:
$s1 = “Another Instance Currently Running...”
$s2 = “Removing Self Executable...”
$s3 = “web_reporter::main_sender_proc()”
$s4 = “NO stat available for “
$s5 = “Please, just wait...”
$s6 = “.cfgETD”
condition:
uint16(0) == 0x457F and
filesize > 1900KB and
all of them
}
Defray777 | RansomEXX
**https://github.com/ditekshen/detection/blob/ce5df37e50b52ddb58dc7ff9b1ab9e011822f68c/yara/malware.yar#L2536**
rule MALWARE_Linux_RansomExx {
meta:
author = "ditekshen"
description = "Detects RansomEXX ransomware"
clamav_sig = "MALWARE.Linux.Ransomware.RansomEXX"
strings:
$c1 = "crtstuff.c" fullword ascii
$c2 = "cryptor.c" fullword ascii
$c3 = "ransomware.c" fullword ascii
$c4 = "logic.c" fullword ascii
$c5 = "enum_files.c" fullword ascii
$c6 = "readme.c" fullword ascii
$c7 = "ctr_drbg.c" fullword ascii
$s1 = "regenerate_pre_data" fullword ascii
$s2 = "g_RansomHeader" fullword ascii
$s3 = "CryptOneBlock" fullword ascii
$s4 = "RansomLogic" fullword ascii
$s5 = "CryptOneFile" fullword ascii
$s6 = "encrypt_worker" fullword ascii
$s7 = "list_dir" fullword ascii
$s8 = "ctr_drbg_update_internal" fullword ascii
condition:
uint16(0) == 0x457f and (5 of ($s*) or 6 of ($s*) or (3 of ($c*) and 3 of ($s*)))
}
HelloKitty | ViceSociety
**https://github.com/signalblur/detection-artifacts/blob/main/yara/linux_malware.yar**
rule HelloKitty {
meta:
description = "linux_ransomware - file HelloKitty"
author = "signalblur"
reference = "Linux Research"
date = "2023-07-17"
hash1 = "556e5cb5e4e77678110961c8d9260a726a363e00bf8d278e5302cb4bfccc3eed"
strings:
$s3 = "esxcli vm process kill" ascii
$s4 = "work.log" ascii
$s7 = "esxcli vm process list" fullword ascii
$s8 = "Error InitAPI !!!" fullword ascii
$s9 = "error encrypt: %s rename back:%s" fullword ascii
$s10 = "No Files Found !!!" fullword ascii
$s11 = "%d manual !!!" fullword ascii
$s12 = "Log closed :%s" fullword ascii
$s13 = "%ld - Files Found " fullword ascii
$s15 = "Total VM run on host:" fullword ascii
condition:
uint16(0) == 0x457f and filesize < 200KB and
4 of them
}
**https://github.com/advanced-threat-research/Yara-Rules/blob/master/ransomware/RANSOM_Linux_HelloKitty0721.yar**
rule ransom_Linux_HelloKitty_0721 {
meta:
description = "rule to detect Linux variant of the Hello Kitty Ransomware"
author = "Christiaan @ ATR"
date = "2021-07-19"
Rule_Version = "v1"
malware_type = "ransomware"
malware_family = "Ransom:Linux/HelloKitty"
hash1 = "ca607e431062ee49a21d69d722750e5edbd8ffabcb54fa92b231814101756041"
hash2 = "556e5cb5e4e77678110961c8d9260a726a363e00bf8d278e5302cb4bfccc3eed"
strings:
$v1 = "esxcli vm process kill -t=force -w=%d" fullword ascii
$v2 = "esxcli vm process kill -t=hard -w=%d" fullword ascii
$v3 = "esxcli vm process kill -t=soft -w=%d" fullword ascii
$v4 = "error encrypt: %s rename back:%s" fullword ascii
$v5 = "esxcli vm process list" fullword ascii
$v6 = "Total VM run on host:" fullword ascii
$v7 = "error lock_exclusively:%s owner pid:%d" fullword ascii
$v8 = "Error open %s in try_lock_exclusively" fullword ascii
$v9 = "Mode:%d Verbose:%d Daemon:%d AESNI:%d RDRAND:%d " fullword ascii
$v10 = "pthread_cond_signal() error" fullword ascii
$v11 = "ChaCha20 for x86_64, CRYPTOGAMS by <appro@openssl.org>" fullword ascii
condition:
( uint16(0) == 0x457f and filesize < 200KB and ( 8 of them )
) or ( all of them )
}
**https://github.com/ditekshen/detection/blob/ce5df37e50b52ddb58dc7ff9b1ab9e011822f68c/yara/malware.yar#L7707**
rule MALWARE_Linux_HelloKitty {
meta:
author = "ditekSHen"
description = "Detects Linux version of HelloKitty ransomware"
strings:
$s1 = "exec_pipe:%s" ascii
$s2 = "Error InitAPI !!!" fullword ascii
$s3 = "No Files Found !!!" fullword ascii
$s4 = "Error open log File:%s" fullword ascii
$s5 = "%ld - Files Found " fullword ascii
$s6 = "Total VM run on host:" fullword ascii
$s7 = "error:%d open:%s" fullword ascii
$s8 = "work.log" fullword ascii
$s9 = "esxcli vm process kill" ascii
$s10 = "readdir64" fullword ascii
$s11 = "%s_%d.block" fullword ascii
$s12 = "EVP_EncryptFinal_ex" fullword ascii
$s13 = ".README_TO_RESTORE" fullword ascii
$m1 = "COMPROMISED AND YOUR SENSITIVE PRIVATE INFORMATION WAS STOLEN" ascii nocase
$m2 = "damage them without special software" ascii nocase
$m3 = "leaking or being sold" ascii nocase
$m4 = "Data will be Published and/or Sold" ascii nocase
condition:
uint16(0) == 0x457f and (6 of ($s*) or (2 of ($m*) and 2 of ($s*)) or 8 of them)
}
Royal
**https://github.com/signalblur/detection-artifacts/blob/main/yara/linux_malware.yar**
rule Royal {
meta:
description = "royal_linux - file Royal"
author = "signalblur"
reference = "Linux Research"
date = "2023-07-17"
hash1 = "b57e5f0c857e807a03770feb4d3aa254d2c4c8c8d9e08687796be30e2093286c"
strings:
$s1 = "esxcli vm process kill" fullword ascii
$s2 = "If you are reading this, it means that your system were hit by Royal ransomware." ascii
$s3 = "esxcli vm process list" ascii
$s4 = ".onion" ascii
$s5 = ".royal_u" ascii
$s6 = ".royal_w" ascii
condition:
uint16(0) == 0x457f and filesize < 7000KB and
2 of them
}
Blacksuit
**https://github.com/signalblur/detection-artifacts/blob/main/yara/linux_malware.yar**
rule BlackSuit {
meta:
description = "linux_ransomware - file BlackSuit"
author = "signalblur"
reference = "Linux Research"
date = "2023-07-17"
hash1 = "1c849adcccad4643303297fb66bfe81c5536be39a87601d67664af1d14e02b9e"
strings:
$e1 = "esxcli vm process kill" ascii
$e2 = "esxcli vm process list" ascii
$r1 = "blacksuit" ascii
$r2 = "BlackSuit" ascii
$w1 = "Terned off vmsyslog" ascii
$w2 = "ps -Cc|grep vmsyslogd > PS_syslog_" ascii
$w3 = "Entropy collected!" ascii
$w4 = "Drop readme failed: %s(%d)" ascii
condition:
uint16(0) == 0x457f and
filesize < 8000KB and
(1 of ($e*) or 1 of ($r*) or 2 of ($w*))
}
Hive
**https://github.com/elastic/protections-artifacts/blob/main/yara/rules/Linux_Ransomware_Hive.yar**
rule Linux_Ransomware_Hive_bdc7de59 {
meta:
author = "Elastic Security"
id = "bdc7de59-bf12-461f-99e0-ec2532ace4e9"
fingerprint = "415ef589a1c2da6b16ab30fb68f938a9ee7917f5509f73aa90aeec51c10dc1ff"
creation_date = "2022-01-05"
last_modified = "2022-01-26"
threat_name = "Linux.Ransomware.Hive"
reference_sample = "713b699c04f21000fca981e698e1046d4595f423bd5741d712fd7e0bc358c771"
severity = 100
arch_context = "x86"
scan_context = "file, memory"
license = "Elastic License v2"
os = "linux"
strings:
$a = { 40 03 4C 39 C1 73 3A 4C 89 84 24 F0 00 00 00 48 89 D3 48 89 CF 4C }
condition:
all of them
}
GonnaCry
**https://github.com/elastic/protections-artifacts/blob/main/yara/rules/Linux_Ransomware_Gonnacry.yar**
rule Linux_Ransomware_Gonnacry_53c3832d {
meta:
author = "Elastic Security"
id = "53c3832d-ceff-407d-920b-7b6442688fa9"
fingerprint = "7d93c26c9e069af5cef964f5747104ba6d1d0d030a1f6b1c377355223c5359a1"
creation_date = "2021-01-12"
last_modified = "2021-09-16"
threat_name = "Linux.Ransomware.Gonnacry"
reference_sample = "f5de75a6db591fe6bb6b656aa1dcfc8f7fe0686869c34192bfa4ec092554a4ac"
severity = 100
arch_context = "x86"
scan_context = "file, memory"
license = "Elastic License v2"
os = "linux"
strings:
$a = { 55 48 89 E5 48 83 EC 10 48 89 7D F8 EB 56 48 8B 45 F8 48 8B }
condition:
all of them
}
Erebus
**https://github.com/Yara-Rules/rules/blob/master/malware/RANSOM_Erebus.yar**
rule Erebus: ransom
{
meta:
description = "Erebus Ransomware"
author = "Joan Soriano / @joanbtl"
date = "2017-06-23"
version = "1.0"
MD5 = "27d857e12b9be5d43f935b8cc86eaabf"
SHA256 = "0b7996bca486575be15e68dba7cbd802b1e5f90436ba23f802da66292c8a055f"
ref1 = "http://blog.trendmicro.com/trendlabs-security-intelligence/erebus-resurfaces-as-linux-ransomware/"
strings:
$a = "/{5f58d6f0-bb9c-46e2-a4da-8ebc746f24a5}//log.log"
$b = "EREBUS IS BEST."
condition:
all of them
}
eChOraix | QNAPCrypt
**https://github.com/intezer/yara-rules/blob/master/QNAPCrypt.yar**
rule QnapCrypt
{
meta:
copyright = "Intezer Labs"
author = "Intezer Labs"
reference = "https://www.intezer.com"
strings:
$a = "Do NOT remove this file and NOT remove last line in this file!" nocase
$b0 = "main.writemessage"
$b1 = "inf.1st.3ds.3fr.4db.4dd.602.a4p.a5w.abf.abw.act.adr.aep.aes.aex.aim.alx.ans.apk.apt.arj.aro.arw.asa.asc.ase.asp.asr.att.aty.avi.awm.awp.awt.aww.axd.bar.bat.bay.bc6.bc7.big.bik.bin.bit.bkf.bkp.bml.bok.bpw.bsa.bwp.bz2.c++.cab.cas.cat.cdf.cdr.cer.cfg.cfm.cfr.cha.chm.cms.con.cpg.cpp.cr2.crl.crp.crt.crw.csp.csr.css.csv.cxx.dap.das.dat.db0.dba.dbf.dbm.dbx.dcr.der.dll.dml.dmp.dng.doc.dot.dwg.dwk.dwt.dxf.dxg.ece.eml.epk.eps.erf.esm.ewp.far.fdb.fit.flv.fmp.fos.fpk.fsh.fwp.gdb.gho.gif.gne.gpg.gsp.gxk.hdm.hkx.htc.htm.htx.hxs.idc.idx.ifx.iqy.iso.itl.itm.iwd.iwi.jcz.jpe.jpg.jsp.jss.jst.jvs.jws.kdb.kdc.key.kit.ksd.lbc.lbf.lrf.ltx.lvl.lzh.m3u.m4a.map.max.mdb.mdf.mef.mht.mjs.mlx.mov.moz.mp3.mpd.mpp.mvc.mvr.myo.nba.nbf.ncf.ngc.nod.nrw.nsf.ntl.nv2.nxg.nzb.oam.odb.odc.odm.odp.ods.odt.ofx.olp.orf.oth.p12.p7b.p7c.pac.pak.pdb.pdd.pdf.pef.pem.pfx.pgp.php.png.pot.ppj.pps.ppt.prf.pro.psd.psk.psp.pst.psw.ptw.ptx.pub.qba.qbb.qbo.qbw.qbx.qdf.qfx.qic.qif.qrm.r3d.raf.rar.raw.re4.rim.rjs.rsn.rss.rtf.rw2.rw3.rwl.rwp.saj.sav.sdb.sdc.sdf.sht.sid.sie.sis.sko.slm.snx.spc.sql.sr2.src.srf.srw.ssp.stc.stl.stm.stp.sum.svc.svg.svr.swz.sxc.t12.t13.tar.tax.tbl.tbz.tcl.tgz.tib.tor.tpl.txt.ucf.upk.url.vbd.vbo.vcf.vdf.vdi.vdw.vlp.vmx.vpk.vrt.vtf.w3x.wav.wb2.wbs.wdb.web.wgp.wgt.wma.wml.wmo.wmv.woa.wpd.wpp.wps.wpx.wrf.x3f.x_t.xbl.xbm.xht.xla.xlk.xll.xlm.xls.xlt.xlw.xml.xpd.xpm.xps.xss.xul.xwd.xws.xxx.zfo.zip.zul.zvz"
$b2 = "main.makesecret"
$b3 = "main.chDir"
$b4 = "main.writemessage"
$b5 = "main.randSeq"
$b6 = "main.encrypt"
condition:
$a or 2 of ($b*)
}
Cylance Ransomware
**https://github.com/signalblur/detection-artifacts/blob/main/yara/linux_malware.yar**
rule Cylance {
meta:
description = "linux_ransomware - file Cylance"
author = "signalblur"
reference = "Linux Research"
date = "2023-07-17"
hash1 = "d1ba6260e2c6bf82be1d6815e19a1128aa0880f162a0691f667061c8fe8f1b2c"
strings:
$s1 = "Usage: %s /path/to/be/encrypted" fullword ascii
$s2 = "Unexpected error %d on netlink descriptor %d (address family %d)." fullword ascii
$s3 = "you will lose your time and data" ascii
$s4 = "@onionmail.com" fullword ascii
$s5 = "relocation processing: %s%s" fullword ascii
$s6 = "Its just a business." ascii
condition:
uint16(0) == 0x457f and filesize < 3000KB and
4 of them
}
RTM Locker
**https://www.uptycs.com/blog/rtm-locker-ransomware-as-a-service-raas-linux**
rule Uptycs_Ransomware_RTM_Locker
{
meta:
malware_name = "RANSOMWARE"
description = "Ransomware is a malware that encrypts sensitive information on your system and asks for ransom in exchange for restoring the encrypted data."
author = "Uptycs Inc"
version = "1"
strings:
$Ransomware_RTM_Locker_0 = "esxcli vm process list" ascii wide
$Ransomware_RTM_Locker_1 = "vmlist.tmp.txt" ascii wide
$Ransomware_RTM_Locker_2 = "esxcli vm process kill" ascii wide
$Ransomware_RTM_Locker_3 = "!!! Warning!!!" ascii wide
$Ransomware_RTM_Locker_4 = "Your network is infected by the RTM Locker command" ascii wide
condition:
all of ($Ransomware_RTM_Locker*)
}
Polaris
**https://github.com/signalblur/detection-artifacts/blob/main/yara/linux_malware.yar**
rule Polaris {
meta:
description = "linux_ransomware - file Polaris"
author = "signalblur"
reference = "Linux Research"
date = "2023-07-17"
hash1 = "e29aa629bf492a087a17fa7ec0edb6be4b84c5c8b0798857939d8824fa91dbf9"
strings:
$x1 = "Inf.css.gif.htm.jpg.mjs.pdf.png.svg.xml" ascii
$x2 = ".avif.html.jpeg.json.ssh/.wasm.webp" ascii
$x3 = "PolarisRadicalReferer" ascii
$x4 = "WARNING.txt" ascii
$x5 = "polaris" ascii
$x6 = "@tutanota.com" ascii
$x7 = "@opentrash.com" ascii
$x8 = "pol.aris" ascii
$x9 = "!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!" ascii
condition:
uint16(0) == 0x457f and filesize < 13000KB and
4 of ($x*)
}
Already have an account? Sign in
No spam, no sharing to third party. Only you and me.